I almost forgot to introduce the new version to the foreign audience, so i going to fix it right now, after a few months. Before you read the latest news of the project i want to summarize some facts you obviously didn't know about Intercepter-NG. It's the first app ever that has:
1. Native and fully functional implementation of SSLStrip for Windows.
2. Automated MiTM attack on SSH2 protocol.
3. Fully functional implementation of a Group Policy Hijacking technique.
4. SMB Hijacking technique and first SMBRelay on NTLMv2.
5. DNS over ICMP MiTM or 'full-duplex icmp redirect' attack.
6. Half-automated ability to sniff valuable information from iOS devices by means of combining different techniques.
7. Powerful and stable LDAP Relay technique.
8. MySQL LOAD DATA Injection technique.
...
---
At last, after ten years of development (yes, this is the project’s age) Intercepter-NG version index reached 1.0. According to a well-established tradition, Windows updates are released once a year and this anniversary release proved to be very successful. I want to thank everyone who assisted me in testing, provided thorough feedback and creatively inspired the project throughout these years.
Let’s start this review with some minor features saving the best for last.
1. Export of selected packets to a .pcap file is added to the RAW Mode. With the Autosave function turned on the packets containing authorization data will be recorded into an individual .pcap file.
2. You can now type several port numbers divided by commas into the Extra SSL Ports field referred to in SSL MiTM.
3. When applying the LDAP Relay attack on a domain controller that utilizes a language other than English, you can manually indicate the required group for adding a user in the expert settings. For example, instead of Domain Admins you can enter its Russian counterpart Администраторы домена.
4. The bug that didn’t allow bruteforcing up the password correctly in some NTLMv2SSP hashes is fixed.
5. Multiple improvements of the Bruteforce Mode. Added: SSL for HTTP support, UTF8 support for bruteforcing LDAP. Also added: VNC, Vmware Auth Daemon and RDP protocols. RDP bruteforce now functions on Windows 7/8/2008/2012. NLA and logins/passwords in any language are supported. RDP Security Layer is not supported.
6. Multiple general improvements and changes. Spoofing is now turned off by default.
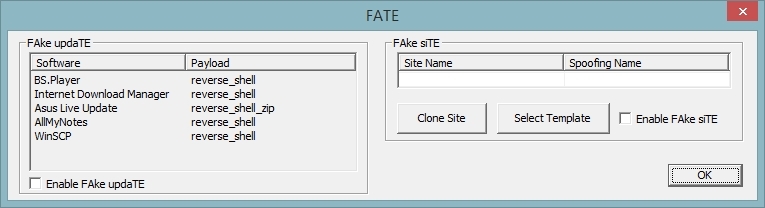
FATE
The FATE mode contains two new functions: FAke siTE and FAke updaTE.
The main purpose of FAke siTE is to obtain authorization data from any web-resource bypassing SSL and other defense mechanisms. It is achieved by means of authorization page cloning and creation of a template to be stored on an embedded pseudo web-server. You can see the workflow on a video at the end of this post. By default, one template for accounts.google.com is included into the Intercepter, because the original page requires filling in firstly the login and then the password. The template however has some minor changes in order to make both fields active simultaneously. Prior to the attack, it is necessary to indicate the domain for the template to be stored. When the attack is commenced a redirect to the selected domain is injected into the victim’s traffic and afterwards the Intercepter automatically executes DNS spoofing to the target addresses. Example site cloning routine for mail.yandex.ru is shown in the video.
Linux fans are familiar with the Evilgrade tool that allows exploiting automatic update mechanism and inject arbitrary payload. Actually, this vector is highly overestimated. First of all, the imposing list of applications supported by the Evilgrade is for the most part out of date. Secondly, a vast majority of the most popular applications check updates using safe routines. Nevertheless, we all heard of infamous flaws in update mechanisms of software produced by large vendors. Probably such things will happen in future as well. Hence the addition of an Evilgrade equivalent to Intercepter-NG. The list of supported software is fairly limited. If required, one’s own templates can be added. You can see their structure in mics\FATE\updates. Please, send me example software that updates openly, we’ll jointly enlarge the database.
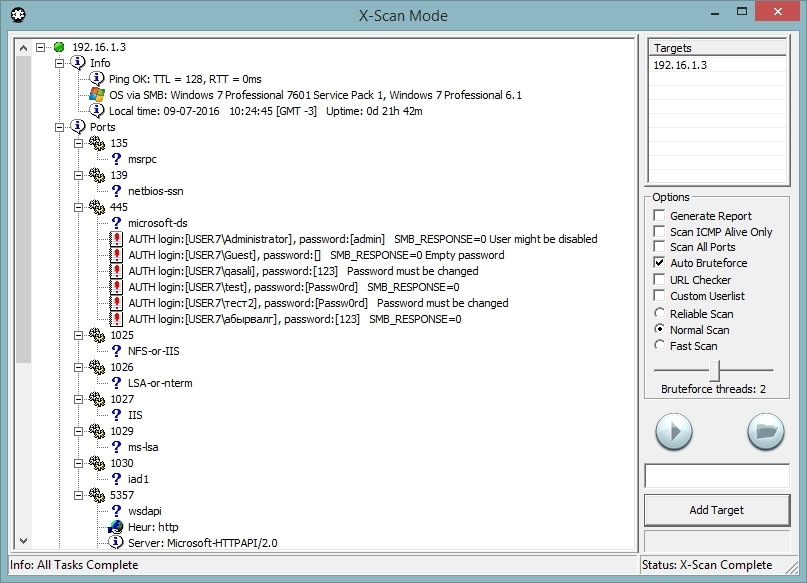
X-Scan
I used to like a network security scanner ‘X-Scan’ developed by a Chinese team Xfocus. It is lightweight, it has a friendly interface and a good functionality. In the middle of the 2000’s it allowed doing lots of things, but then its development stopped and nowadays it is not very useful. This is why I wanted to create its contemporary equivalent, but it just didn’t work out… until recently. Paying respect to the original software the network scanner appears in Intercepter-NG under the same name.
The scanner is a replacement for the primitive port scanner from previous versions. Let’s see what it is capable of.
1. Scan open ports and determine heuristically the following protocols: SSH, Telnet, HTTP\Proxy, Socks4\5, VNC, RDP.
2. Determine the presence of SSL on an open port, read banners and different web headers.
3. Upon finding a proxy or a SOCKS check if they are open outwards.
4. Check access to VNC servers without password, check SSL for HeartBleed bug. Read DNS version.bind.
5. Check availability of potentially vulnerable to ShellShock scripts on a web-server according to the base. Check a list of directories and files for 200 OK and the list of directories from robots.txt according to the base.
6. Determine OS version through SMB. Obtain local time, uptime and the list of common resources and local users if anonymous access is allowed. Automatic passwords bruteforce is launched for the identified users.
7. Determine SSH users according to the embedded list by analyzing response time. Automatic passwords bruteforce is launched for the identified users. If the enumeration didn’t find any (the enumeration doesn’t function on every version) the bruteforce launches only for the root.
8. Automatic bruteforce for HTTP Basic and Telnet. False alarms are possible because of telnet protocol features.
It is possible to scan any targets in local networks as well as the Internet. You can enter a list of ports for scanning: 192.168.1.1:80,443 or a range: 192.168.1.1:100-200. It is also possible to enter an address range for scanning: 192.168.1.1-192.168.3.255.
In order to obtain more accurate results only three hosts can be scanned at the same time. Verifications for data from SSL certificates were added literally in the last minute. For example, if the word Ubiquiti is encountered and the port 22 is open bruteforce of SSH user ubnt launches automatically. The same applies for a pair of Zyxel hardware with a user ‘admin’.
For the first release of the scanner, its features are sufficient and they are fine-tuned pretty well. Send me your ideas and suggestions.

нажимаешь не те кнопки видимо.
ОтветитьУдалитьЗдравствуйте, давно искал программу , но никак не понимаю, как установить ? Через TOR скачал , а открыть не может даже Zip. Подскажите пожалуйста , хочу дальше в этой сфере развиваться .
ОтветитьУдалитьа тор то нахрена? пробуй с гитхаба.
УдалитьУ меня кнопка скан по ходу не работает и меню где Smart scan не появляется
ОтветитьУдалить